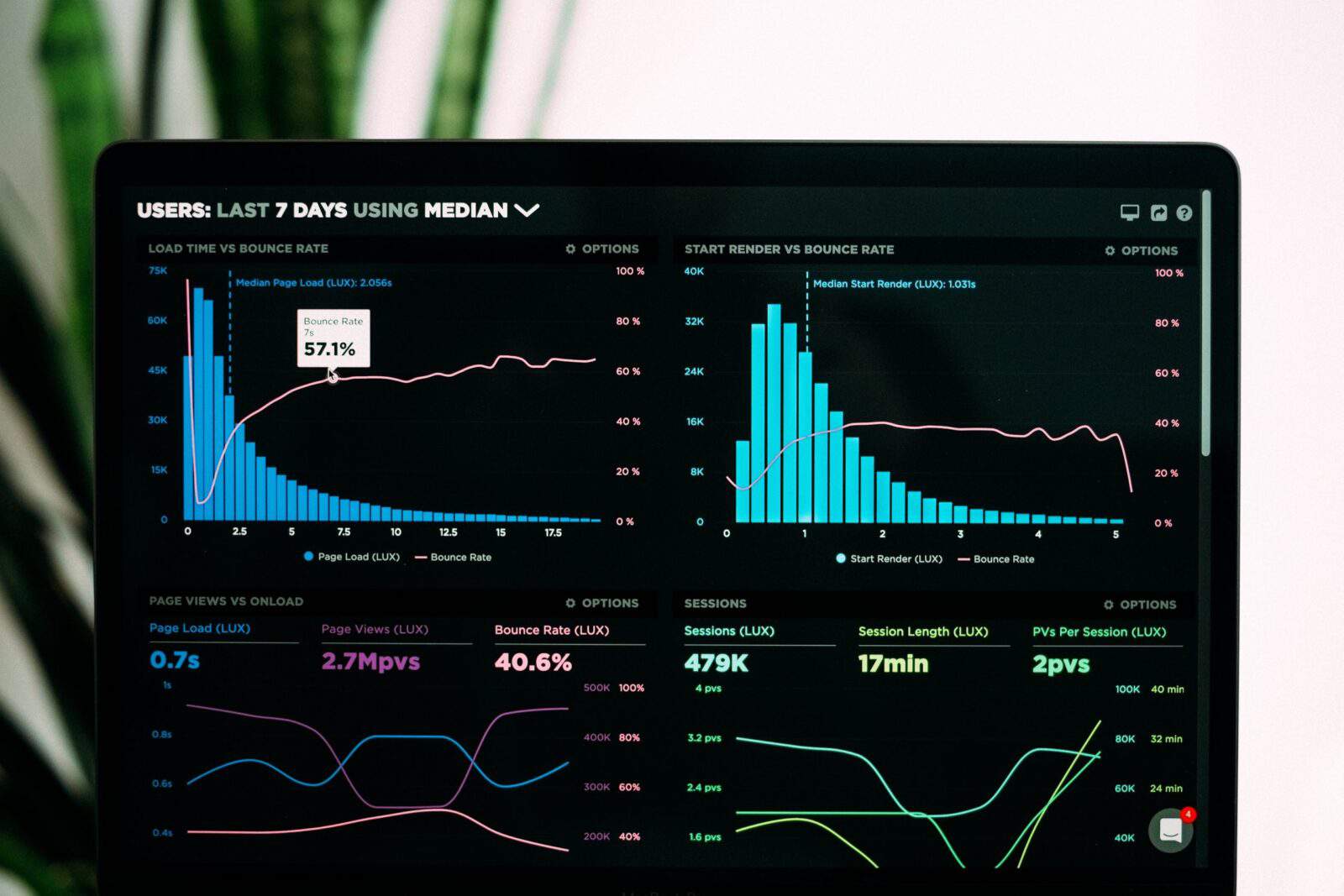
Staying ahead in the dynamic realm of cybersecurity is paramount. The traditional notion of a security perimeter, once a stalwart defense for our networks and data, is losing its reliability. Understanding how Cisco’s Security Service Edge (SSE) is reshaping cybersecurity strategies becomes pivotal as cyber threats evolve in complexity and reach.
Read on to explore the landscape of cybersecurity services, dissecting the looming threats and unraveling the essence of Cisco’s Security Service Edge.
Evolving Cybersecurity Landscape
In the recent past, a robust firewall and reliable antivirus software protected a business’s digital assets. These defenses, essentially the security perimeter, acted as a fortress. However, the terrain has shifted. These defensive walls have weakened with the advent of cloud computing, the surge in remote work, and the pervasive use of IoT devices.
The expansion of digital footprints for businesses has unexpectedly widened the scope for cybercriminals. Phishing attacks, malware, ransomware, and other tools have become commonplace in a cyber attacker’s portfolio. These threats can now infiltrate networks from within, bypassing traditional perimeter defenses.
Understanding Cybersecurity Services
In response to the escalating complexity of cyber threats, businesses have recognized the need to bolster their cybersecurity measures. They now adopt a multifaceted strategy integrating various services seamlessly to combat diverse threats.
The Role of Cybersecurity Services
Cybersecurity services encompass a spectrum of tools and techniques, from intrusion detection and prevention systems to identity and access management. The primary aim is to identify vulnerabilities, fortify defenses against breaches, and swiftly respond to mitigate damages in case of a breach.
The Emergence of Security Service Edge
In cybersecurity evolution, the emergence of Cisco’s Security Service Edge (SSE) marks a significant turning point, signaling a shift in our approach. SSE isn’t just another tool in the cybersecurity toolbox; instead, it is a comprehensive strategy that reshapes the entire cybersecurity landscape.
Cisco SSE encompasses a suite of technologies designed to secure access to web, cloud services, and private applications, irrespective of user location, device used, or application hosting. It includes threat protection, data security, access control, security monitoring, and acceptable-use control enforced through network-based and API-based integration.
The Array of Cisco SSE Tools
The traditional security perimeter has become outdated. SSE’s array of tools signifies a new phase in cybersecurity, where dynamic and integrated defenses replace the old-fashioned concept. Let’s dive into these tools to understand how SSE transforms cybersecurity strategies:
Secure Web Gateway (SWG)
The Secure Web Gateway (SWG) is a virtual administrator for network access, monitoring access points, and filtering information to remove potentially dangerous items while upholding strict security guidelines.
Zero Trust Network Access (ZTNA)
ZTNA adopts a skeptical approach to network security. Unlike the traditional model that assumes trust once a user enters the network, ZTNA treats every access attempt with suspicion. It demands verification of the user’s identity and trustworthiness, even for those already within the network boundaries. This proactive stance aims to enhance security by reducing the potential for unauthorized access or compromised identities.
Firewall-as-a-Service (FWaaS)
FWaaS is a robust shield to strengthen data security. Its primary role is to block unauthorized access, ensuring the complete integrity and safety of data in a system or network. This service is a barrier against possible threats by managing and overseeing incoming and outgoing traffic, upholding a secure environment.
Cloud Access Security Broker (CASB)
A Cloud Access Security Broker (CASB) is a shield for cloud-based applications, actively overseeing and securing sensitive data. It upholds security standards by monitoring activities in these apps, acting as a gatekeeper to enforce protective measures and policies. Its primary task is safeguarding valuable information from threats or unauthorized access.
Impact of Cisco’s SSE on Cybersecurity Redefinition
How does SSE influence the reshaping of cybersecurity strategies? Here are vital ways Cisco SSE brings about this transformation:
Minimizing Risks with Advanced Cybersecurity
SSE integrates multiple defense layers against cyber threats, reducing risks and preventing a single point of failure from compromising security.
Simplifying End-User Experience
With a unified access approach, SSE simplifies secure access to any application, bidding farewell to complex and frustrating access procedures.
Streamlining IT Operations
Imagine managing all security and networking needs from a single console. SSE streamlines policy management and reporting, simplifying IT operations.
Ensuring Business Continuity
The cost of a cybersecurity breach surpasses financial losses; it can influence a company’s reputation. SSE ensures business continuity, shielding against the aftermath of a breach.
SSE vs. SASE: Navigating the Differences
Secure Access Service Edge (SASE) emerged as a concept introducing a new approach to network security, aiming to redefine the relationship between Secure Service Edge (SSE) and SASE.
SSE (Security Service Edge)
SSE is a comprehensive approach to cybersecurity that focuses on securing access to web services, cloud applications, and private applications, regardless of user location, device used, or application hosting. Below are the critical components of SSE.
- Threat Protection: Guards against cyber threats.
- Data Security: Ensures the security of sensitive data.
- Access Control: Regulates who can access what.
- Security Monitoring: Constant surveillance for potential risks.
- Acceptable-Use Control: Enforces policies via network-based and API-based integration.
SASE (Secure Access Service Edge)
SASE is a holistic approach to security and networking that combines traditional network security services, such as firewall, VPN, and intrusion detection and prevention, with cloud-based security services, including CASB and ZTNA. Check out the below components of SASE to better understand it:
- Unified Platform: Integrates traditional and cloud-based security services.
- Network Security Services: Includes firewall, VPN, intrusion detection, and prevention.
- Cloud-Based Security Services: Involves CASB and ZTNA.
Choosing Between SSE and SASE
Deploying SSE or moving towards a complete SASE topology depends on network infrastructure, procurement teams, contracts, and specific use cases. An incremental approach is also feasible, starting with SSE and gradually transitioning to a complete SASE solution.
Incremental Approach
Commencing with SSE and gradually progressing towards a complete SASE solution offers a pragmatic transition, ensuring security and networking needs are met seamlessly. The traditional security perimeter is no longer relevant. Cisco’s Security Service Edge is a game-changer in today’s digitally-driven world, where cyber risks are a significant concern. SSE redefines cybersecurity strategies by offering advanced protection, simplifying access, streamlining operations, preserving business continuity, and fortifying private applications.
It’s time to reframe your cybersecurity strategy and transcend the perimeter with Cisco’s SSE. Capital Techies Managed IT Services can help you implement robust Cisco SSE cybersecurity solutions to safeguard your business. Contact us now.